Dealing with Social Media Impersonation
Social media platforms have become important in shaping personal and professional digital identities, but they are also ripe pickings for social media impersonation. Not only is impersonation against the terms of use of social media platforms, but this form of impersonation attacks not only challenge one’s carefully crafted online presence but also pose reputational risks that can wreck your digital footprint.
This article explores strategies Reputation X uses to tackle social media impersonation.
Understanding Social Media Impersonation
Impersonation on social media takes several forms:
- Personal Account Impersonation: Individuals craft profiles mirroring real individuals using publicly available information. This form aims to deceive the impersonated individual’s network for malicious gain. For example, they may copy a profile photo and use it for their impersonation account.
- Social Media Account Hijacking: Legitimate accounts are compromised (hacked) and then used to propagate harmful content or to gain someones trust, like your friends for example. This often happens as the result of a data breach.
- Fake Accounts or Bots: These are automated accounts designed to amplify misleading information, spread malware, or engage in provocative activities. They are often backed by powerful AI.
- Executive and Brand Impersonation: Attackers impersonate executives or brands to mislead stakeholders or to scam consumers by mimicking official communications. For example, they may set up a look-alike site similar to the brand to steal logins. When this happens to people, we call them social doppelgangers.
Impersonation thrives due to the ease with which attackers can exploit personal information. It is often sourced from data breaches. Attackers use techniques like credential stuffing or brute-forcing to get unauthorized access to social media accounts.
Risks of Social Media Impersonation
Key Risks of Social Media Impersonation:
- Reputation Damage: The immediate and long-term impact on an individual’s or brand’s reputation can be devastating, influencing public perception and trust.
- Identity Theft and Financial Fraud: Impersonators often work for financial gain, using stolen identities for fraudulent transactions that can lead to substantial financial losses for victims
- Legal Consequences / Emotional Toll: Victims of impersonation may experience cyberbullying and social engineering attacks, as well as the stress of navigating legal processes to seek damages or the removal of impersonating accounts.
Strategies to Deal with Impersonation
To effectively deal with social media impersonation, a multifaceted approach is essential. Here are strategic measures to consider:
- Preventive Measures:
- Limit personal information shared online. It’s difficult for impersonators to copy a photo without one to copy.
- Make social media accounts private if you can (tough for brands)
- Use strong passwords and enable two-factor authentication (2FA).
- Monitor online presence for unauthorized accounts or profiles. Here are some examples as to where to do this:
- Active Response Strategies:
- Report fake accounts to social media platforms immediately (see links above).
- Change all passwords and monitor for unusual activities.
- Use third-party security applications for automated monitoring and brand protection. Here are some examples:
- Consider online brand protection services from Reputation X for defense against impersonation.
- Post-Incident Actions:
- Document the impersonation without contacting the impersonator.
- Warn your contacts and report the impersonation to the respective platform.
- Review and update security measures to prevent future incidents.
By implementing these strategies, individuals and organizations can reduce the risk of social media impersonation.
Impersonation Response
When confronting social media impersonation, immediate and comprehensive action is important in order to mitigate its effects and protect one’s digital identity. The response can be summarized in a series of strategic steps:
- Documentation and Reporting:
- Document the Evidence: Take screenshots of the impersonating social profiles, messages, or any other relevant interactions as you might need these to prove reputational risk or for legal reasons.
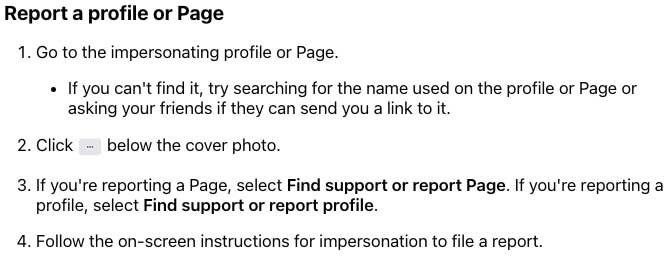
- Report to Social Media Platforms: Utilize the platform’s reporting feature to alert them of the impersonation, leveraging their policies against such activities. See the links above.
- Contact Authorities: For serious threats or financial fraud, report to law enforcement to initiate an investigation.
- Inform and Secure:
- Warn Your Contacts: Alert your network to the impersonation to prevent them from being deceived.
- Check Other Accounts: Review your other social media and financial accounts for unusual activities, making sure all are secure.
- Use Online Privacy Services: Consider employing privacy services to monitor and protect your digital footprint.
- Legal Considerations:
- Consider Legal Action: If damages are incurred, consulting with a legal professional to explore options for recourse might be necessary. Reputation X can make recommendations in this regard.
- Platforms’ Review Process: Understand that after reporting, social media platforms will review the case and take action to remove impersonating accounts, a process that varies in response time.
Social media impersonation is a pain. But, by following these steps, people and organizations can respond to impersonation, protecting their reputation and minimizing potential reputational harm.
